Prerequisites: Knowledge on ARP process. [http://www.erg.abdn.ac.uk/users/gorry/course/inet-pages/arp.html]
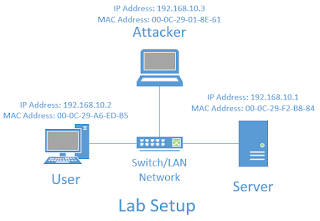
Lab Setup for ARP Poisoning

Now the attacker does a ARP Poisoning in the network, now the ARP tables changes as below:

ARP Poisoning: Server and User will be communicating with the attacker PC even though they think they are communicating with each other. This kind of attack can be easily be detected with the help of Packet Analyzer or checking the ARP table.
Wireshark Analysis on ARP Poisoning

When apply ICMP, we get the response from the destination but the path is via Attacker PC. As you can see the wireshark packet capture, packet from User is going Attacker then its going to destination and via versa.
Also, Attacker learns the layer 2 information on the LAN segment and changes the ARP table.
[ For more details - http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6500-series-switches/white_paper_c11_603839.html ]
Lab Setup for ARP Poisoning
In this lab we are assuming that the Attacker is compromised the network, so its in same LAN segment.
Normal ARP between User and Server will have ARP cache (table) as below:
- User PC
- Server

Now the attacker does a ARP Poisoning in the network, now the ARP tables changes as below:
- User PC
- Server

ARP Poisoning: Server and User will be communicating with the attacker PC even though they think they are communicating with each other. This kind of attack can be easily be detected with the help of Packet Analyzer or checking the ARP table.
Wireshark Analysis on ARP Poisoning

When apply ICMP, we get the response from the destination but the path is via Attacker PC. As you can see the wireshark packet capture, packet from User is going Attacker then its going to destination and via versa.
Also, Attacker learns the layer 2 information on the LAN segment and changes the ARP table.
[ For more details - http://www.cisco.com/c/en/us/products/collateral/switches/catalyst-6500-series-switches/white_paper_c11_603839.html ]
★CT21